We have developed a unique methodology of adapting your process for delivery on your engagements while ensuring that the security of your information is maintained.
Process
Every business functions in a manner that is unique to itself and the cost of change can be counter-productive and ineffective. Hence we believe in adapting your process so that we can become a true extension of your office and deliver our services seamlessly. That said, we do also believe in being guided by an efficiency driven process to ensure expectations of our clients are met and that there are no surprises.
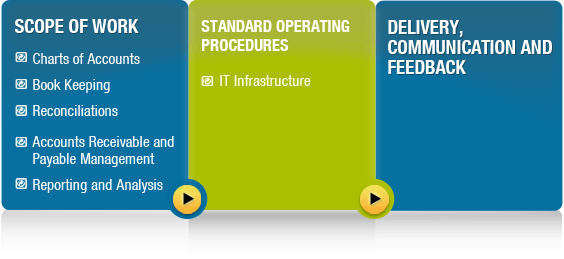
At the onset of any engagement, we identify the detailed services or scope of work which could include setting up charts of accounts, book-keeping, general ledger, accounts management, reconciliations, invoicing, etc.
Once the scope of work is detailed, our team works with you in identifying the infrastructure or tools needed to carry out the tasks. Our team has experience in working with QuickBooks online, remote login into servers, and other third party web applications. At this time, the flow of information is also defined. This includes everything from identifying how source data (invoices, statements, etc.) will be provided by the client, the way entries need to be made into relevant systems, how the data needs to be backed up, etc.
The team then manages close contact with the client by providing daily updates on tasks done and a summarized report on a weekly basis along with timesheet information. Instructions and information can be provided via email, fax, shipping physical documentation or though our online task management tool.
Security
We provide a secure environment where client records are safe and are kept confidential.
- Non Disclosure Agreement signed with all team members at a general and an engagement specific level
- Work is carried out in a secure workplace and is not accessible to people outside the organization
- Team members are not allowed to either bring in or to take out any material. All belongings are checked in at the locker room before entering the secure work place. All material needed to execute assignments are provided and retained within the workplace
- Firewall and Anti-virus Software
- Access to Internet on project machines is restricted to MSTSC and/or Citrix environment (if applicable)
- Restricted email access
- Daily backup (only in case of minimum automation process and on client’s instruction)
- Data Destruction (those residing on our premises) on client’s instruction
![]()
Kaushik has been doing a really great job and I rely heavily on his help with the financials, so I would hate to lose him!
Thanks!

Jennifer Muniz
iVital

